System Setup:
The underlying finite field will be F24 and the elliptic curve is described by the following equation: E = y2 + xy = x3 + g3 (here: a = 0, b = g3)
The point P = (xP, yP) = (g5, g11) is selected. Since 5P = O, the point P has the order n = 5. The public information (system parameters) are the field of F24, the curve E, the point P, and the order n = 5.
Key Generation (done prior to ECES)
Party A performs the following operations:
- A selects a random integer d = 3 in the interval [2, n-2] = [2,3]
- A computes the point Q = dP = 3(g5,g11) = (g,0) = ((1100),(0000))
- A makes public the point Q.
- A's private key is the integer d.
Encryption Process
Party B performs the following steps in order to send the message M = 010100 to Party A:
- B looks up A's public key: Q = (xQ, yQ) = (g,0).
- B selects a random integer k = 2 in the interval [n, n-2] = [2,3] - the private key for the one-time key pair.
- B computes the point (x1,y1) = kP = 2(g5,g11) = (g,g) = ((1100),(1100)) - the public key for the one-time key pair.
- B computes the point (x2,y2) = kQ = 2(g,0) = (g5,g11) = ((1010),(1110)). x2 is the secret value.
- B generates a mask Y of length 6 with the mask generation function from the secret value x2. Depending of the mask generation function used, Y will vary. For the purposes of this example, let Y = 011010.
- B computes C = Y
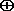 M = (011010)
M = (011010) 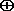 (010100) = (001110)
(010100) = (001110)
- B computes the encrypted message by concatenating (x1,y1) and C and transmits (11001100001110) to Party A
Party A performs the following steps in order to decrypt the ciphertext EM = 11001100001110 received from B.
- A uses the first 8 bits of the string for the one-time public key: ((1100),(1100)). The rest of EM will be stored in C.
- A computes the point (x2,y2) = d(x1,y1) = 3(1100,1100) = 3(g,g) = (g5,g11) = ((1010),(1110)). x2 is the secret value.
- Using the same mask generation function as B, A generates from x2 the mask Y = 011010.
- A recovers the message M by XORing all but the first 8 bits of EM with the mask Y: M = C
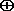 Y = (001110)
Y = (001110) 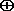 (011010) = (010100)
(011010) = (010100)

![[back]](back.gif)
![[previous menu]](square.gif)
![[next]](next.gif) .
.