(continued)
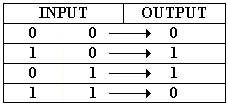
The message can be finally encrypted by combining the message bit-string M with the mask bit-string Y though an "exclusive-or" function. An exclusive-or function (often denoted by XOR or 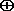 ) takes each bit from each string and replaces it with one bit according to the following rule: output 1 if either bit is 1, but not both.
) takes each bit from each string and replaces it with one bit according to the following rule: output 1 if either bit is 1, but not both.
For example: if the message M = 00110101 and the mask Y = 10010001,
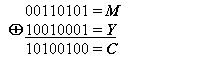
Then the cyphertext C is C = Y 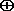 M
M
It is this cyphertext bit-string C that is transmitted to Alice.
A remarkable characteristic of the XOR function is that when it is re-applied to the output, the original bit-string is obtained. Here: M = C 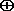 Y. Reapplying the mask Y to the cyphertext C will result in the original message, M.
Y. Reapplying the mask Y to the cyphertext C will result in the original message, M.
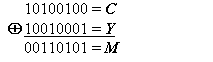
Since Alice also knows that secret value z, she can apply it to the same masking function that Bob used to create the mask Y. By applying the XOR function to the mask and cyphertext bit-strings, Alice decrypts the cyphertext back into the original message, M.

![[back]](back.gif)
![[previous menu]](square.gif)
![[next]](next.gif) .
.